What is Wfuzz?
According to docs:
"Wfuzz has been created to facilitate the task in web applications assessments and it is based on a simple concept: it replaces any reference to the FUZZ keyword by the value of a given payload."
What this means is that it can be used to facilitate content discovery and brute forcing for security researchers.
Installation
sudo pip3 install --upgrade wfuzz
Use Cases
There are 3 main use cases for wfuzz for me.
Content Discovery on a single host.
Finding live hosts for subdomain discovery.
Brute Forcing a parameter.
For content discovery in a single host I also use dirsearch with a custom dictionary but wfuzz also really works well combined with SecLists for a more targeted approach. You can find dictionaries curated by many information security professionals at https://github.com/danielmiessler/SecLists.
I often run wfuzz in the following way for content discovery:
:~/SecLists/Discovery/Web-Content$ wfuzz -t 100 -c -z file,raft-medium-files-lowercase.txt --hc 404,403,500 https://example.com/FUZZ
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: https://example.com/FUZZ
Total requests: 16243
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000061: C=200 50 L 120 W 1270 Ch "index.html"
000366: C=200 50 L 120 W 1270 Ch "."
Total time: 143.9259
Processed Requests: 16243
Filtered Requests: 16241
Requests/sec.: 112.8566
To break this command down, first -t option specifies how many threads we want to create(use this sparingly if you don't want to create too much noise) -c just produces colorful output --hc is used to hide the status code of responses you don't want to see, another way to filter would be using --sc where you only print status codes you want to see. Filtering allows us to see only the results we care about, which is very important for content discovery as we have to minimize the noise to focus on valid endpoints on the website. Finally we specify the domain we want to find files on and wfuzz replaces the FUZZ keyword with what's in the file you passed into it.
You can use this to quickly discover directories and files on a single host.
Second use case is finding subdomains. My approach to subdomains with wfuzz looks like this:
Get a list of CNAMEs from a public dataset
Parse this list for the target host and grab all known CNAME's pointing to and from the domain.
Send a request to every possible subdomain on the list with wfuzz.
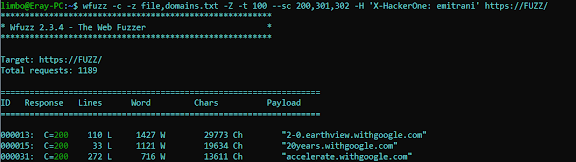
wfuzz -c -z file,domains.txt -Z -t 100 --sc 200,301,302 -H 'X-HackerOne: emitrani' https://FUZZ/
Finally brute forcing is a fairly simple use case where you want to maximize the number of threads you are using. It is also possible to make wfuzz generate your payloads but I usually just stick to quick Python scripts to generate the inputs I want and just pass wfuzz a text file with the payloads I generated.
For example brute forcing an admin panel from a curl request can be converted to wfuzz will look like the following case:
curl 'https://example.com/admin' -H 'authority: ' -H 'cache-control: max-age=0' --data 'login=admin&password=hunter12' --compressed
--------------------------------------------------------------------
wfuzz -z file,passwords.txt --hc 403,429 -t 100 -d 'login=admin&password=FUZZ' -H 'authority: ' -H 'cache-control: max-age=0' https://example.com/admin
Wfuzz is a really versatile tool and it can be used in a lot of situations but hopefully this blog post gave you some ideas to where and when it might be useful.

No comments:
Post a Comment